Congress asks more questions about TSA blacklists
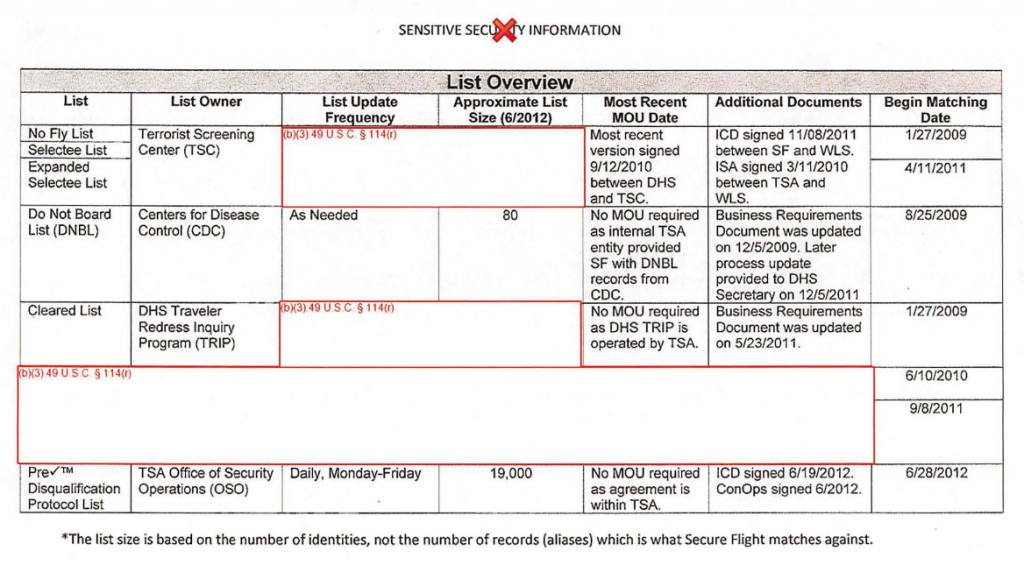
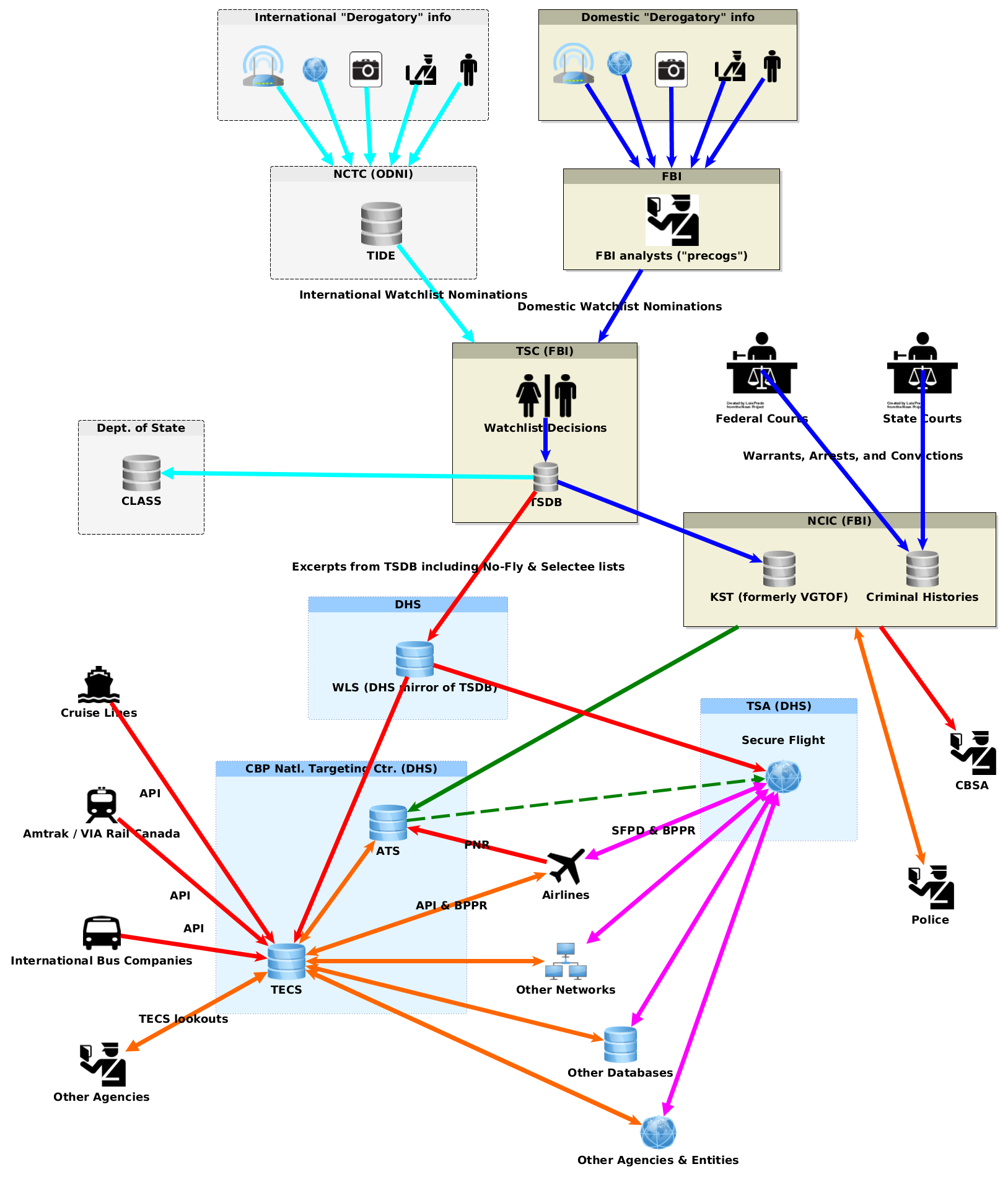
The “No-Fly” and “Selectee” lists managed by Federal agencies through the joint Watch List Advisory Council (WLAC) aren’t the only blacklists and watchlists that are used to determine who is given US government permission to board an airline flight, and how they are treated when they fly.
Senior members of relevant House and Senate Committees are asking overdue questions about the blacklists created and used by the Transportation Security Administration (TSA) to target selected travelers for special scrutiny, surveillance, and searches when they fly.
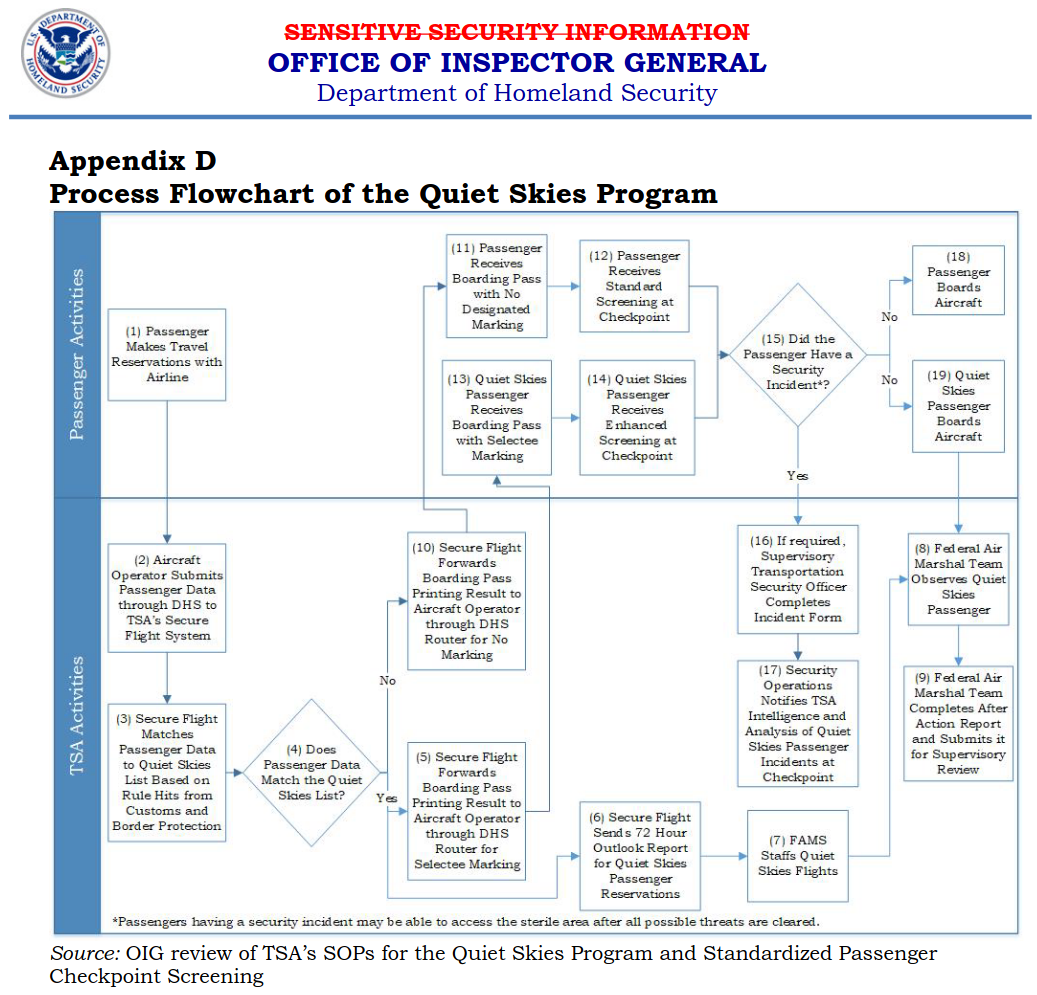
The TSA’s Secure Flight program is used to determine, on the basis of identifying and itinerary information from ID documents and airline reservations, what Boarding Pass Printing Result (BPPR) to send to the airline for each would-be passenger. The ruleset included in the Secure Flight algorithm includes list-based and profile-based Quiet Skies rules created by the TSA itself, independent of the interagency No-Fly and Selectee travel blacklists.
These Quiet Skies rules are used to flag certain airline passengers as “Selectees” to be searched more intrusively at TSA checkpoints (even if they aren’t on the interagency Selectee list), and to assign Federal Air Marshals (FAMs) to follow, watch, and file reports on their activities in airports and on flights. A secret alert is sent to FAMs, based on airline reservations, 72 hours before each planned flight by a person on the Quiet Skies list.
The Quiet Skies program was implemented secretly in 2012. “In March 2018,” according to a later report on the Quiet Skies program by the DHS Office of Inspector General (OIG), “in addition to enhanced checkpoint screening, TSA began surveillance (observation and collection of data) of Quiet Skies passengers beyond security checkpoints, as part of its Federal Air Marshal Service’s (FAMS) Special Mission Coverage flights.
The No-Fly list and profile-based no-fly rules are used in the Secure Flight travel control and surveillance algorithm to determine who is allowed to fly. The Selectee and Quiet Skies lists and rules are used to determine who to search and surveil when they fly.
The Quiet Skies program came to light later in 2018 when FAM whistleblowers went to the Boston Globe with their complaints that the wrong travelers were being targeted, mis-prioritizing which flights FAMs were being assigned to. These FAM whistleblowers complained, that, for example, anyone identitied from airline reservations as having traveled to Turkey was put on the Quiet Skies list and had a FAM assigned to each US flight they took for the next several months, including domestic flights. Travelers’ reports of being followed through airports (presumably by FAMs) and subjected to more intusive searches at TSA checkpoints after trips to Turkey supported these allegations.
The TSA initially declined to confirm the existence of the Quiet Skies program. But in response to questions from Congress and follow-up reprting by the Globe, the TSA released a belated Privacy Impact Assessement (PIA) for Quiet Skies in 2019. However, that PIA specified none of the Quiet Skies rules and gave no demographic or other information about who those rules had targeted.
Additional descriptions of the program, including the flowchart above, but still not including any of the Quiet Skies rules, were included in a critical DHS OIG report on the program in 2020.
Since January 6, 2021, there has been a new round of complaints by travelers and disgruntled FAMs that participants in the activities that day at the US Capital have been put on the No-Fly, Selectee, and/or Quiet Skies lists.
This month a redacted version was made public of a formal complaint to the DHS OIG by a FAM who says his wife was put on the Quiet Skies list and “targeted for FAMS ‘Special Mission Coverage’ simply because she attended President Trump’s January 6, 2021 speech at the ellipse in Washington, D.C.” FAMs also said that former US Representative and Presidential candidate Tulsi Gabbard has been put on the Quiet Skies list because of her role in the January 6, 2021 events. When she read those reports, Gabbard said that, “The whistleblowers’ account matches my experience” of disprate treatment at TSA checkpoints.
We’ve been unable to confirm or disprove these reports. But we find them plausible and — whether or not they are true — indicative of fundamental problems in these arbitrary, secret, extrajudicial schemes for making decisions about the exercise of our right to travel by common carrier and to be free from unreasonable searches and seizures.