CBP keeps its app for US visitors secret
Should a visitor to the US have to install and use a US government app that runs secret code to collect an unknown amount of data using any or all of their phone’s sensors, connects to other unknown data sources and recipients, and uses secret algorithms based on that secret dataset to “auto-deny” some ESTA applications to visit the USA?
We say no — and so does US law.
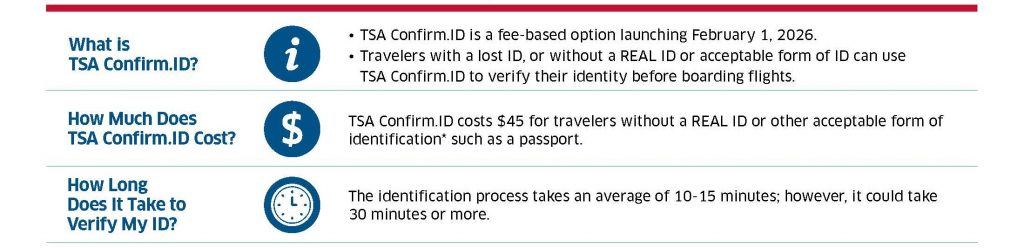
In December 2025, US Customs and Border Protection (CBP) announced that it planned to shift the Electronic System for Travel Authorization (ESTA) from a website to an app, greatly expand the range of data collected from ESTA applicants, and delegate authority to the app to “auto-deny” some applications.
CBP proposed no rules to govern the proposed “auto-denial” of ESTA applications. We can find no basis in any law for such an automated decision-making procedure. But CBP gave notice that it intends to seek approval for this new and revised app-based collection of ESTA information from the Office of Management and Budget (OMB).
According to the Paperwork Reduction Act (PRA), the request for OMB approval must be preceded by notice of the proposed collection of information, followed by a window of at least 60 days for members of the public to review and submit comments on the proposal.
PRA regulations at 5 CFR §1320.8(d)(2) require that this notice include a complete copy of the proposed collection of information or instructions on how any member of the public can obtain a copy, free of charge, and still have 60 days to review and comment on the proposal.
But CBP didn’t include a copy of the code or any other part of the ESTA app in any format in its notice in the Federal Register. As the 60-day notice-and-comment window runs out, CBP still has not responded to our repeated requests for this information.
As we note in the comments we filed with CBP:
Since the day this notice was published in the Federal Register we have been diligently, but to date entirely unsuccessfully, attempting to request and obtain a copy of the proposed collection of information from the points of contacts specified in the notice.
This isn’t just a procedural error. The failure to provide valid notice denies us and all other members of the public the opportunity to provide informed comment on the ESTA app, which would require an expert review and audit of the source code.
As of now, we’ve seen none of the user interface screens of the proposed ESTA app; none of the PRA, Privacy Act, administrative appeal rights and procedures, and/or other notices (if any) provided to users of the app; none of the code specifying what data is collected, transmitted, and received by the app; and none of the code embodying the algorithms and specifying the data they use as the basis for “auto-denial” of some ESTA applications.
The proposal for collection of more information and robo-adjudication of the equivalent of visa applications would be a bad idea even if PRA procedures were followed. We’ll have much more to say about these proposals if and when CBP provides us with proper notice and a chance to inspect the workings of the proposed new version of the ESTA app.
If you’re an Android and/or iOS app developer who might be willing to volunteer your expertise to help us analyze and audit the workings of the ESTA app, if CBP ever publicly discloses its code, please get in touch.
But as of now, because the notice was plainly invalid, OMB can’t legally approve the CBP proposal.
CBP must either withdraw or abandon this proposal or provide a valid new notice, with a complete copy of the ESTA app including its source code, followed by a new 60-day comment period. If CBP submits this proposal to OMB without first doing this, OMB must reject it as being in clear violation of the PRA regulations.
CBP isn’t using the standard Regulations.gov system for submission of comments on this proposal. If you want to submit your own comments, send them by email by to CBP_PRA@cbp.dhs.gov by midnight EST Monday, February 9, 2026. Be sure to include “Comments to CBP re: OMB Control Number 1651–0111” in the subject line of your email message.