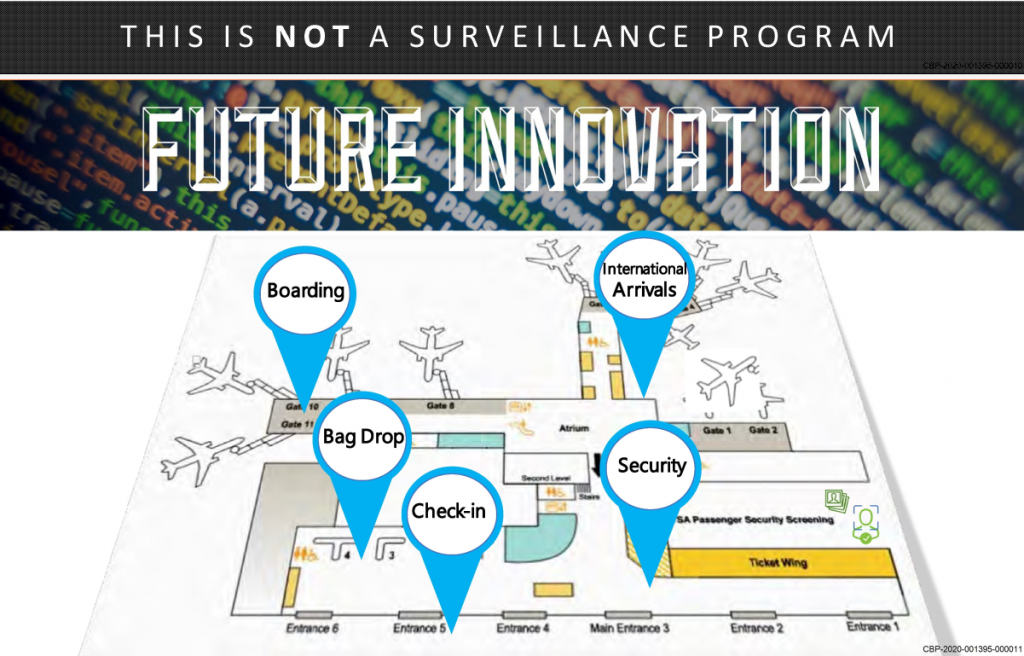
[Email from the Financial Crimes Enforcement Network (FinCEN) of the US Department of the Treasury to some of its banking industry partners forwarding list prepared by Mitsubishi United Financial Group (MUFG) of vendors at DMV (DC, Maryland, and Virginia) airports, train stations, and bus stops, to target reporting of purchases at these locations as “suspicious” .]
[Email from the Financial Crimes Enforcement Network (FinCEN) of the US Department of the Treasury to some of its banking industry partners forwarding list prepared by Mitsubishi United Financial Group (MUFG) of vendors at DMV (DC, Maryland, and Virginia) airports, train stations, and bus stops, to target reporting of purchases at these locations as “suspicious” .]
The House Committee on the Judiciary and its Select Subcommittee on the Weaponization of the Federal Government have released a ground-breaking report on their investigation of what they describe — accurately, we think — as “the coordination between Big Banks and Big Government” in financial surveillance.
The Judiciary Committee and Subcommittee’s latest report on financial surveillance as well as their earlier interim report on the same issue are part of their broader inquiry into the investigative tactics used in the aftermath of the storming of the US Capitol on January 6, 2021.
Partisan criticism of the Weaponization Subcommittee may lead to some skepticism or dismissal of its report and recommendations. But that would be a mistake, regardless of what anyone thinks about the Weaponization Subcommittee in general. The report is thoroughly researched and its sources are well documented. It’s based on interviews with witnesses from goverment agencies and the banking industry and tens of thousands of documents provided in response to Congressional subpoenas.
The report on financial surveillance uses the post-January 6th investigation only as a case study. The practices it reports on could have been, and still could be, used against any of us, regardless of party or affiliation (if any). They shouldn’t be used against anyone, even the most stigmatized individuals and groups. What we allow to be done to our enemies, or anyone’s enemies, could be done to any of us. The report deserves bipartisan public attention and calls for bipartisan action by Congress.
As we’ve noted in surveying what’s likely to lie ahead in demands for ID and ID-based surveillance and control of our real-world and virtual movements and activities, it’s all too easy and all too common for otherwise-principled civil libertarians to allow their distaste for particularly reviled individuals to blind them to the bad precedents being set by the investigative and prosecutorial tactics used against those stigmatized defendants.
We can’t afford to be sanguine about violations of anyone’s rights. The government’s response to the events of January 6, 2021, was a textbook example of the way that unsympathetic defendants are exploited to expand the norms of permissible and publicly-tolerated investigative and prosecutorial practices that can later used more widely.
After January 6th there were misguided calls to add everyone involved in the storming of the Capitol (and perhaps also anyone suspected of possibly having been involved) to the million-and-a-half names already on the US government’s no-fly list — by summary, secret, extrajudical administrative action. It’s unclear whether, or to what extent, that was done. That remains an open question, as does the larger question of how no-fly decisions are made. We hope that the Weaponization Subcommittee and the Subcommittee on the Administrative State will look into these questions during the next session of Congress.
Suspects were targeted for prosecution after January 6th based on what may have been the most extensive use to date in any single investigation of geofence warrants for cellphone location data. Those general warrants were used not to obtain evidence pertaining to individuals who there was already probable cause to suppect of crimes, but to trawl through records of hundreds of millions of innocent cellphone users to find individuals to place under suspicion based on where their cellphones were logged by Google as having been on that day. Challenges to the Constitutionality of these general warrants for dragnet searchess were all — so far as we can tell — dismissed by the judges hearing these cases.
But that’s not all. The latest Judiciary Committee report shows how logs of routine, entirely legal, financial transactions were subjected to warrantless scrutiny and data mining by banks and financial services providers collaborating with government investigators, and used as the basis for placing individuals under suspicion.
The FBI encouraged banking companies to “voluntarily” submit Suspicious Activity Reports (SARSs) to the Financial Crimes Enforcement Network (FinCEN), the police division of the Department of the Treasury. These SARs were used to finger to FinCEN as “suspicious” anyone who had engaged in such mundane activities as taking money out of an ATM, buying a meal at an airport, or paying for a hotel or AirBNB anywhere in the DMV (DC, Maryland, and Virginia) area on January 6th or the days before or after:
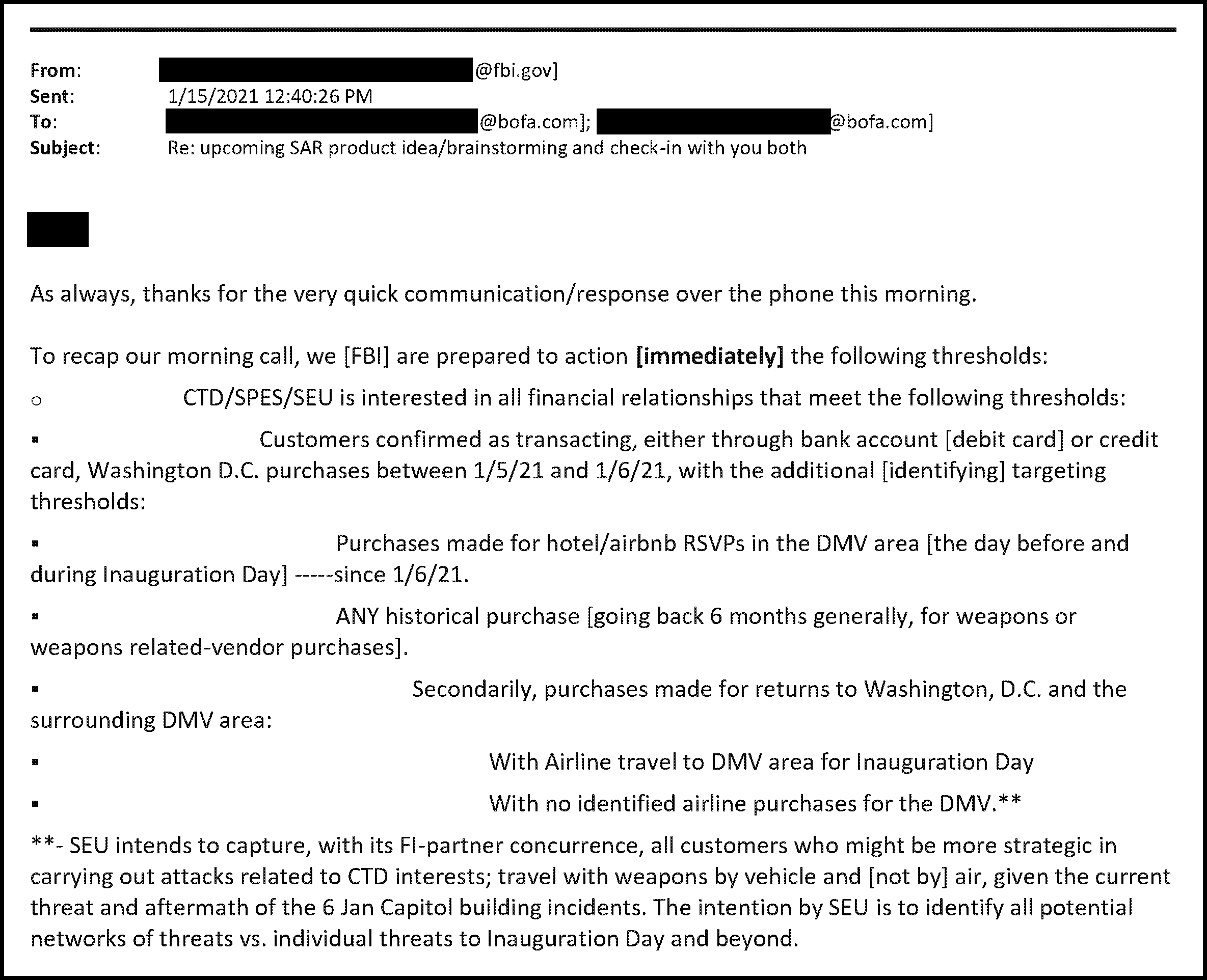
To be clear: these transactions were, in and of themselves, entirely legal, and weren’t in and of themselves in any way suspicious. They didn’t create probable cause to believe that each such individual was likely to have committed any crime, and they wouldn’t have provided sufficient basis for the issuance of a search warrant. These SARs were used not to investigate people who were already suspected of crimes, but to identify new individuals to be extrajudically placed under suspicion and investigated without probable cause.
Once submitted to FinCEN, these SARs are available for individual search and retrieval by tens of thousands of government agents, without the need to apply for a warrant. SAR data is also exported in bulk by FinCen for import into other agencies’ data mining systems.
Read More →
 Edward Hasbrouck of the Identity Project was a guest today with Prof. David Farber (Keio Univ. Cyber Civilization Research Center) and Prof. Dan Gillmor (Arizona State Univ.) for the CCRC / IP-ASIA weekly online gathering on current issues, discussing the expansion of demands for ID, identification as a service provided by the government to commercial entities, the evolution of ID-based surveillance and control, and the human rights work of the Identity Project:
Edward Hasbrouck of the Identity Project was a guest today with Prof. David Farber (Keio Univ. Cyber Civilization Research Center) and Prof. Dan Gillmor (Arizona State Univ.) for the CCRC / IP-ASIA weekly online gathering on current issues, discussing the expansion of demands for ID, identification as a service provided by the government to commercial entities, the evolution of ID-based surveillance and control, and the human rights work of the Identity Project: