GAO audit confirms TSA shift to pre-crime profiling of all air travelers
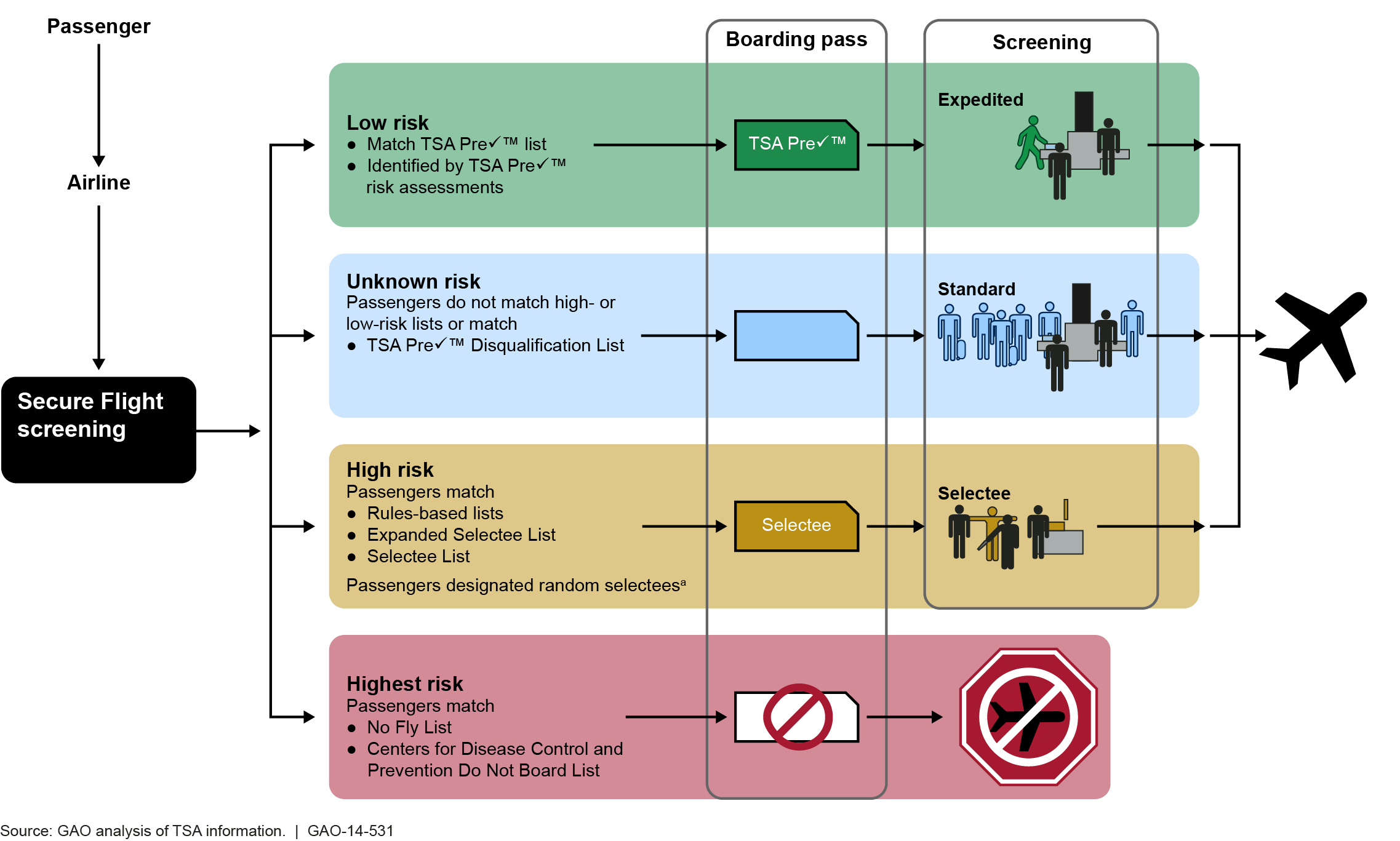
A Congressional hearing last week on the so-called “Secure Flight” system for “screening” domestic air travelers confirmed that the TSA has completed a shift from blacklist and whitelist matching to a comprehensive real-time pre-crime profiling system that assigns each air traveler a “risk assessment” score on the four-step scale we’ve previously described and which is illustrated above in the latest GAO report.
Redacted versions of three audit reports on Secure Flight by the Government Accountability Office (1, 2, 3) were made public in conjunction with GAO testimony at the hearing. According to one of those reports, “Secure Flight” started out as a blacklist and whitelist matching system:
Since implementation began in January 2009, the Secure Flight system has identified high-risk passengers by matching SFPD [against the No Fly List and the Selectee List, subsets of the Terrorist Screening Database (TSDB), the U.S. government’s consolidated watchlist of known or suspected terrorists maintained by the Terrorist Screening Center, a multiagency organization administered by the Federal Bureau of Investigation (FBI)…. To carry out this matching, the Secure Flight system conducts automated matching of passenger and watchlist data to identify a pool of passengers who are potential matches to the No Fly and Selectee Lists. Next, the system compares all potential matches against the TSA Cleared List, a list of individuals who have applied to, and been cleared through, the DHS redress process.
But that’s not how it works any more. According to the same GAO report:
Since January 2009, the Secure Flight program has changed from one that identifies high-risk passengers by matching them against the No Fly and Selectee Lists to one that assigns passengers a risk category: high risk, low risk, or unknown risk. Specifically, Secure Flight now identifies passengers as high risk if they are matched to watchlists of known or suspected terrorists or other lists developed using certain high-risk criteria, as low risk if they are deemed eligible for expedited screening through TSA Pre-Check — a 2011 initiative to preapprove passengers for expedited screening — or through the application of low-risk rules, and as unknown risk if they do not fall within the other two risk categories. To separate passengers into these risk categories, TSA utilizes lists in addition to the No Fly and Selectee Lists, and TSA has adapted the Secure Flight system to perform risk assessments, a new system functionality that is distinct from both watchlist matching and matching against lists of known travelers.
We’ve said from the start that Secure Flight would not be limited to “list matching” and would assign risk scores to all travelers. Now that’s been confirmed by GAO auditors. When the TSA talks about “risk-based screening”, what they mean is “pre-crime profiling” of all air travelers — part of a larger pattern of “predictive” pre-crime policing through surveillance and profiling.
The diagram at the top of this article shows what the GAO says the current “Secure Flight” profiling process, and its consequences, look like. Note the references to “risk assessments” and “rules-based lists”, although in fact these are real-time scoring systems and there are no publicly-disclosed “rules”.