How the DEA uses travel company spies to confiscate travelers’ cash
A report by the Office of the Inspector General (OIJ) of the U.S. Department of Justice (DOJ) sheds more light on how the Drug Enforcement Agency (DEA) pays workers for airlines, Amtrak, bus companies, and package delivery services to spy on their customers, troll through reservation and shipping records, and finger travelers and senders and recipients of packages to the DEA in exchange for a share of the cash which can be seized and “forfeited” to the government even if no drugs are found and no criminal charges are brought.
This practice was first reported in August 2016 by Brad Heath in USA Today, based on case-by-case review of court filings describing the basis for DEA searches that led to “civil forfeiture” proceedings. And the DOJ OIG had released brief interim summaries of its investigations into DEA relationships with one Amtrak employee and one TSA employee who were paid to inform on travelers.
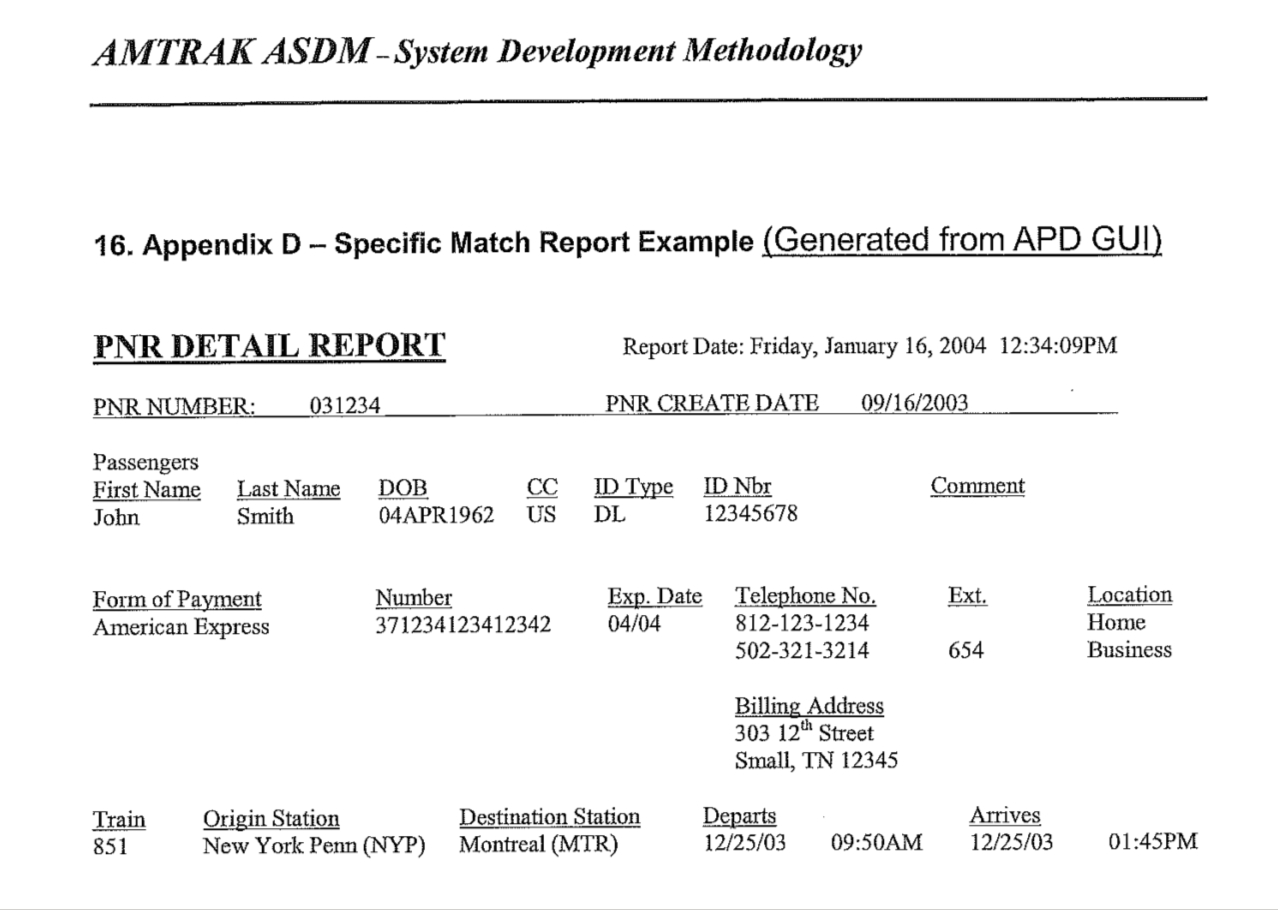
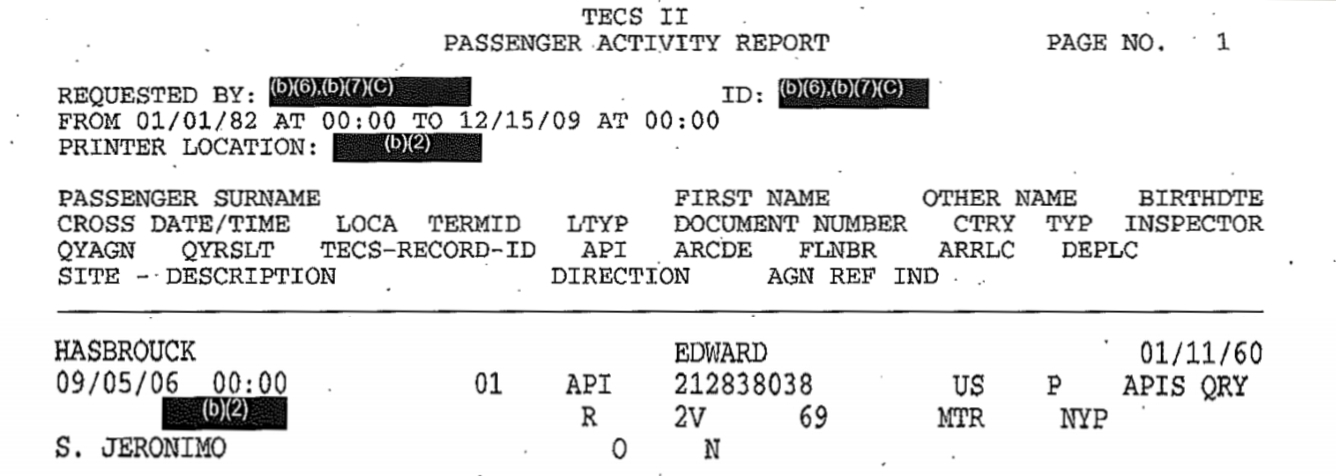
The new OIG report released last week provides much more detail about the scope of the DEA’s use of travel and transportation staff as paid “confidential sources” to target travelers and parcels for cash seizures on the basis of travel reservations and shipping records. The OIG found that the DEA is paying employees of Amtrak, airlines, bus companies, and other transportation companies millions of dollars for individual tips and copies of entire passenger manifests:
[DEA] Special Agents have various ways of receiving these “tips,” but generally receive the information on a daily basis via email or text message, some of which are sent to government accounts and others to non-government private accounts that are established and controlled by the Special Agents. Additionally, we found that although some Special Agents estimated receiving up to 20 “tips,” or passenger itineraries, per day from their… commercial airline confidential sources, the DEA does not maintain a record of receipt of the totality of the confidential source “tips.”….
[S]ome Agents requested that sources provide them with suspicious travel itineraries that met criteria defined by the Agents, and in some cases requested entire passenger manifests almost daily….