Since the start of the post-9/11 shift from case-by-case government access to travel reservations to dragnet surveillance of all reservations and pre-crime profiling of all travelers, the government has claimed repeatedly that the information to which it has demanded access was already “routinely” provided by travelers to airlines and other travel companies.
We’ve recently received some details of just how untrue those claims are, through the latest installment of a continuing trickle of responses by Amtrak to a Freedom Of Information Act request we made in 2014. (See our previous reports on government surveillance of Amtrak passengers.)
Anyone familiar with travel industry practices and reservation data has known all along that the government’s demands for data about airline, train, bus, and cruise ship passengers have exceeded what was needed by common carrier for commercial purposes. Until after September 11, 2001, walk-up customers could buy tickets for cash, for themselves or anyone else, at airline or Amtrak or Greyhound ticket counters, without providing any information at all except an (unverified) name. No address, phone number, or other identifying or contact information was required.
The government has demanded not just access to existing travel industry databases, but the logging of additional details about travelers that were never previously required. The travel industry worldwide has had to spend billions of dollars modifying every layer and component of their IT systems, and of all the systems that interact with them, to collect and store this additional information and deliver it to the government in standardized government-dictated formats.
Even names of travelers weren’t required for reservations, tickets, or travel. Space could be reserved for a group of travelers with only a group identifier or lead contact. Sometimes dummy or placeholder names would be entered for group members, but they could be and often were omitted.
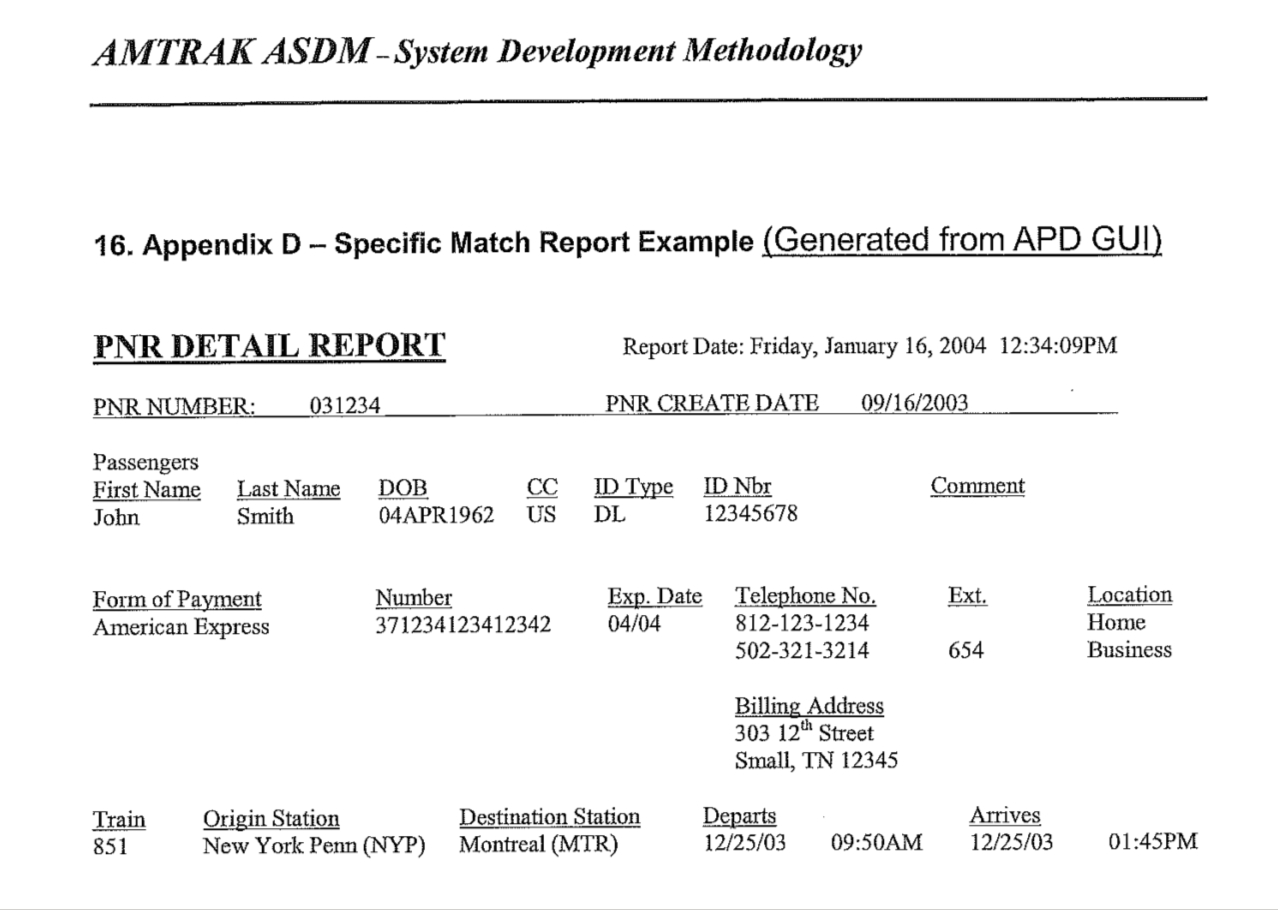
The latest file we’ve received from Amtrak is a PDF of images of printouts or views of email messages (we haven’t received the raw “message source” files we requested, and will eventually be appealing Amtrak’s failure to release them) within Amtrak and between Amtrak, the big four CRS/GDS companies (Sabre, Amadeus, Worldspan, and Galileo/Apollo — then owned by Cendant) and possibly their contractors or other “partners” (names redacted).
These messages date from 2006, when Amtrak “voluntarily” decided to start sending data about all passengers on cross-border Amtrak trains and buses between the USA and Canada to the DHS Advance Passenger Information System (APIS). In order to populate the API data fields, Amtrak decided to make “Passenger ID” (PID) a required field in all Amtrak reservations. That took some work in itself, but it also caused a cascade of new problems for reservations without names, especially those for as-yet-unknown members of groups:
Read More →