The #NoFly list is a #MuslimBan list
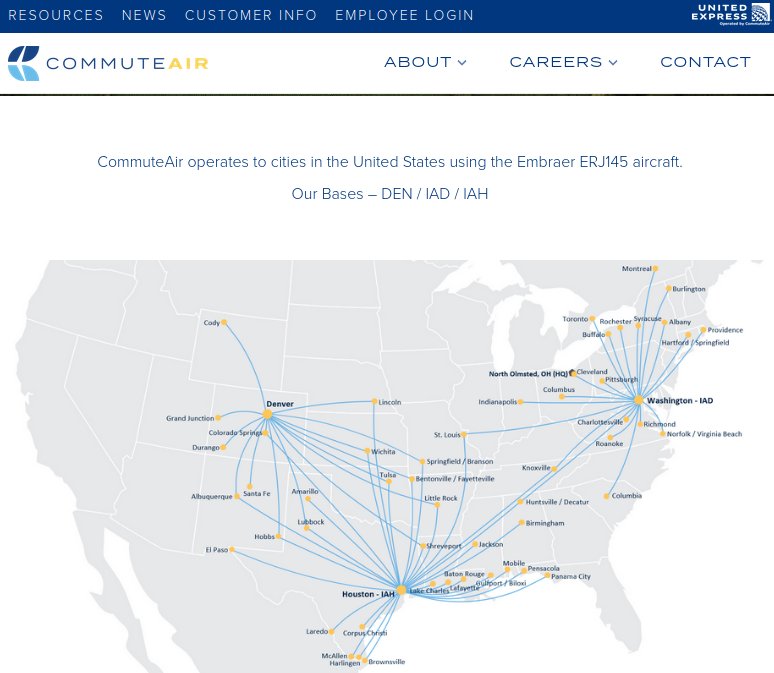 [CommuteAir routes operated as “United Express”]
[CommuteAir routes operated as “United Express”]
In news first reported by Mikael Thalen and David Covucci of of the Daily Dot, Swiss hacker maia arson crimew has found versions of the Transportation Security Administration’s “No-Fly” and “Selectee” lists dating from 2019 on insecure Amazon Web Services cloud servers used by the airline CommuteAir for software development and staging.
CommuteAir is little known in its own name, but operates as a subcontractor to United Airlines for flights by regional jets between United hubs and secondary airports marketed under the “United Express” brand with United Airlines flight numbers.
In a statement to the Daily Dot, CommuteAir confirmed that, “The server contained data from a 2019 version of the federal no-fly list that included first and last names and dates of birth.”
This isn’t the first time that information about the TSA’s “watchlists” (blacklists) and related procedures has been leaked or left exposed on the Internet. In 2009, the TSA posted an unredacted copy of its Standard Operating Procedures for “screening” of airline passengers on a Federal government website for contractors. In 2014, the Terrorist Screening Center’s Watchlisting Guidance, which describes the methodology and purported basis for entering names on the No-Fly, Selectee, and other blacklists, was obtained and published by The Intercept.
The lists found by maia and shared with journalists and researchers confirm the TSA’s (1) Islamophobia, (2) overconfidence in the certainty of its pre-crime predictions, and (3) mission creep.
The data in the files found by maia is limited to first and last name and date of birth and a sequence number for each listing, but there are headers for several other fields that are blank in most of the records: place of birth, citizenship, passport or ID number, “MISC”, and a blank field labeled “CLEARED” which may have been used to indicate those entries that were intended to be to be whitelisted rather than blacklisted.
The most obvious pattern in the data is the overwhelming preponderance of Arabic or Muslim-seeming names. More than 10% of the entries on the No-Fly list (174,202 of 1,566,062) contain “MUHAMMAD” in either the first or last name fields. “It’s just crazy to me how big that Terrorism Screening Database is and yet there is still very clear trends towards almost exclusively Arabic and Russian sounding names throughout the million entries,” maia told the Daily Dot.
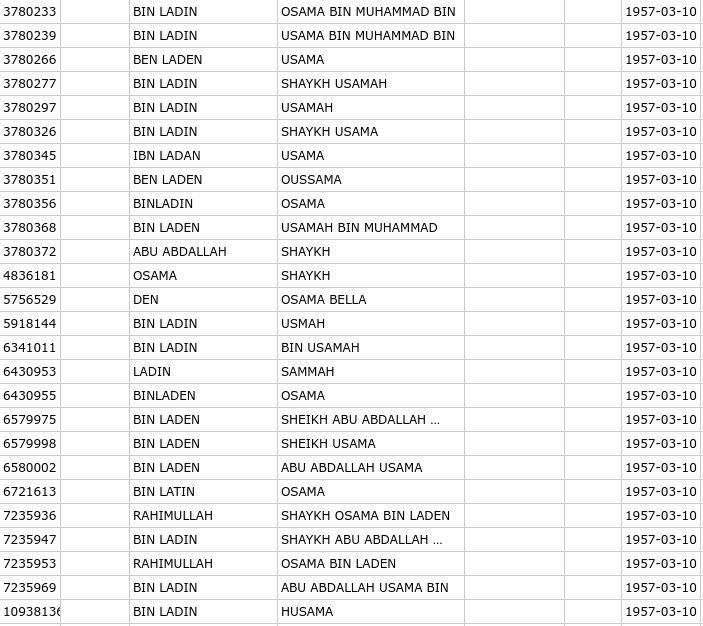 [Some of the listings for Osama Bin Laden — already long dead — on the 2019 No-Fly List]
[Some of the listings for Osama Bin Laden — already long dead — on the 2019 No-Fly List]
The “NOFLY.csv” file found by maia contains 1,556,062 entries. The “SELECTEE.csv” file contains 251,169. The youngest of those on this version of the No-Fly List, as of 2019, were three four-year-olds. The oldest were twenty-five centenarians.