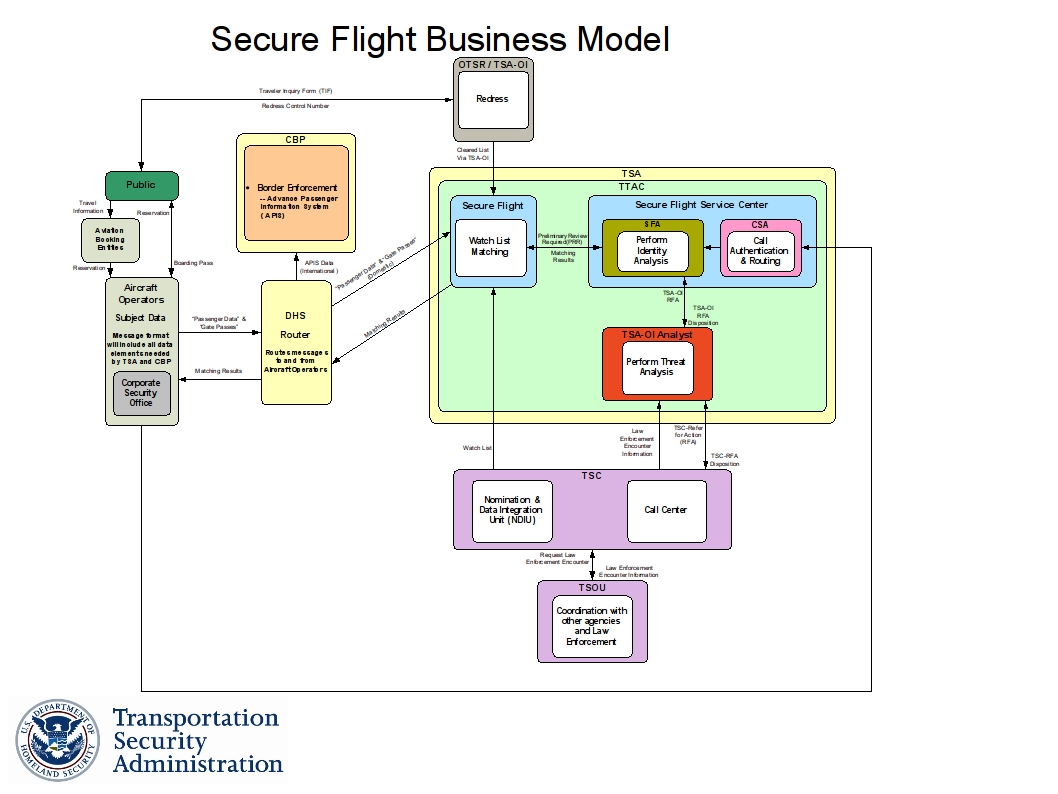
How will “Secure Flight” be enforced?
Recent announcements by airlines suggest that, either on their own initiative or in response to secret Security Directives from the TSA, they are implementing new and clearly illegal Secure Flight enforcement measures.
One of the many questions about the TSA’s Secure Flight program has been how it would be enforced.
None of the published Secure Flight regulations include any enforcement provisions or any provisions imposing obligations on travelers, and the details of Secure Flight implementation are spelled out, if at all, only in secret Security Directives to airlines that by their nature cannot impose any obligations on travelers.
The TSA’s own secrecy leaves us no choice but to rely on whistle-blowers and leakers within the government and the airline industry (please keep those calls, letters, and e-mail messages coming!) and on what we can infer from airlines’ public disclosures.
This new notice from American Airlines is typical of what we’ve been seeing and hearing lately:
As a result of the Transportation Security Administration (TSA) and Department of Homeland Security (DHS) mandate, beginning November 1, all passengers will be required to have Secure Flight Passenger Data (SFPD) in their reservation at least 72 hours prior to departure….
In compliance with this mandate you will be required to provide Secure Flight Passenger Data:
- To purchase any ticket on or after September 15, 2010
- To travel November 1, 2010, or later regardless of purchase date
What’s wrong with this picture?
The “mandate” described on the AA website doesn’t exist in any Federal statute or publicly-disclosed regulation, or in AA’s tariff or contractual conditions of carriage. On the contrary, airlines are required by Federal law to be licensed as common carriers. They are required to sell a ticket to, and to transport, any would-be passenger willing to pay the fare and comply with the rules in their published tariff.
Federal agencies including the TSA and Department of Transportation (DOT) are required when issuing regulations to take into consideration “the public right of freedom of transit” by air, and have no authority to issue administrative regulations or directives that would override the statutory definition of airlines as common carriers.
No court has ever even considered, much less upheld, any suggestion that air travelers forfeit their right to remain silent in response to questions from the TSA or other Federal employees, much less from TSA contractors or airlines.
On international routes, bilateral and multilateral aviation treaties similarly require airlines to operate as common carriers, in accordance with published rules and a published tariff.
So if AA or any other airline refuses to sell you or a ticket, or to transport you, solely on the basis of your declining to provide Secure Flight data, they render themselves liable to Federal civil suit and damages for refusal of transportation in violation of their duty as a common carrier, as well as to formal complaint and revocation of their operating license for the same violation.
While the US government might intervene in US court to block such a suit on the grounds that any Security Directives issued to the airline were a state secret, that wouldn’t be possible if the lawsuit for refusal to transport were brought in the courts of a foreign country from which the airline refused to transport you to the US.
If an airline tried to file new conditions of carriage incorporating such a provision for denial of transportation, the US Department of Transportation would be duty bound, by Federal statute, to disapprove it. And if the DOT approved such a filing applicable to an international route, the government of other affected country or countries would be entitled both to disapprove the filing (by treaty, international tariffs typically require approval by both or all countries involved) and to protest its approval by the US as a treaty violation.
We hope that, faced with these choices and risks, airlines will choose to follow Federal law and international aviation and human rights treaties, and will vigorously and publicly litigate their challenges to any US attempt, through secret Security Directives or otherwise, to get them to depart from their duty to the traveling public as common carriers.