ICE is buying location data from smartphone apps, etc.
How can your movements be tracked?
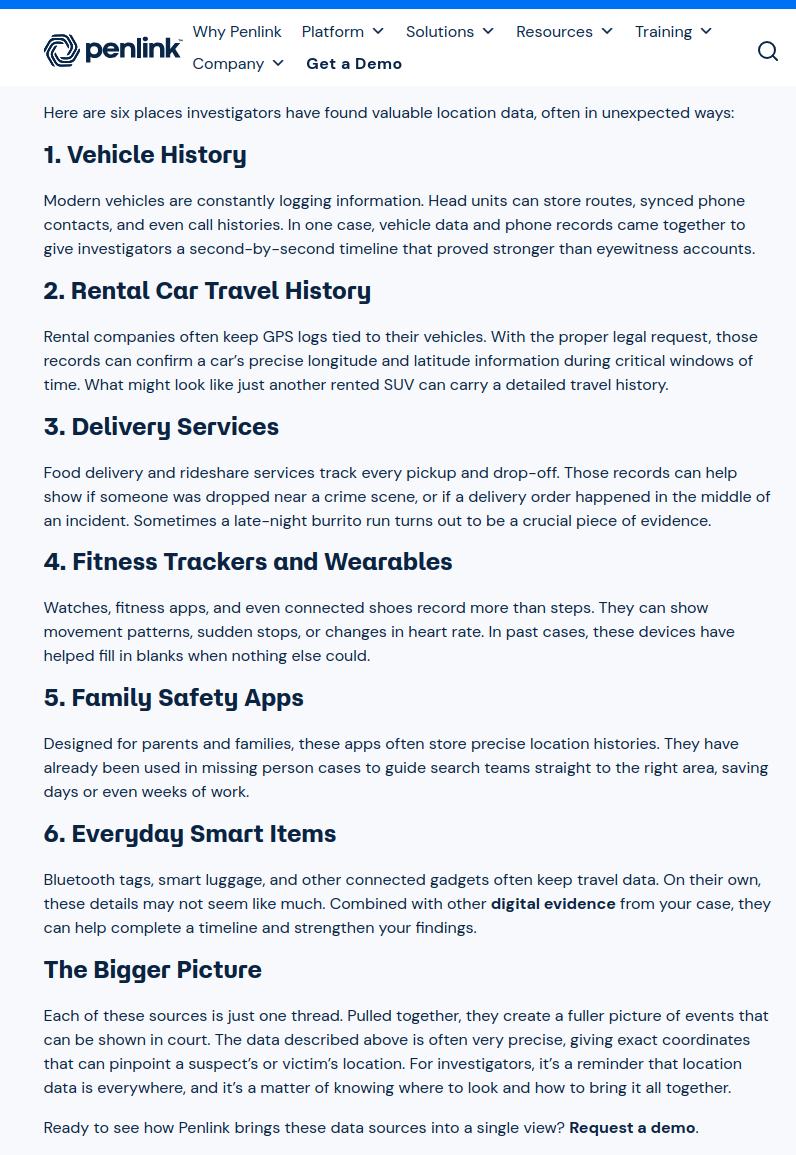
The Penlink surveillance company counts some of the ways:
Penlink was brought to our attention by a report from Joseph Cox in 404 Media that the Immigration and Customs Enforcement (ICE) division of the US Department of Homeland security (DHS) is entering into a contract with Penlink as a unique and irreplaceable source of aggregated location data from smartphone apps and other sources.
According to an ICE document justifying the no-bid single-source contract that was uncovered by 404 Media, Penlink is the only company that can “compile, process, and validate billions of daily location signals from hundreds of millions of mobile devices, providing both forensic and predictive analytics”, and that is willing to sell ICE access to this data.
Penlink also extracts and makes available to its subscribers, in real-time, location data embedded in EXIF metadata in smartphone photos uploaded to Facebook and other social media, and boasts of its ability to aggregate location data from many other sources.
How does Penlink get this data, in order to be able to sell it to ICE?
Most people didn’t (and wouldn’t) knowingly consent to having this information sent to and used by the government, and wouldn’t think of this information as “open source”. How many people even realize that, by default, each smartphone photo contains precise location information included within the image file?
Most people would consider an app that collects timestamped location tracking data and sends it to a company that sells it to the police to be “malware”.
Almost all of these apps with embedded surveillance malware are distributed — in most cases, distributed exclusively — through the Google Play Store or the Apple App Store.
To put it another way, the Google Play Store and the Apple App Store are the primary distribution channels for malware people install on their smartphones that enable government surveillance.
Recently, Google has threatened to require developers to upload scans of government-issued ID documents in order to have their apps installed on any “Google-certified” device.
We doubt that the developers of apps that sell their users’ location data to Penlink and similar data brokers to sell to police and other third parties will be deterred from distributing their surveillance malware by a requirement to show ID to Google.
Google’s demand for developer ID is a threat to developers who don’t want to empower Google and Apple to decide who can and can’t use their software. It’s also a threat to independent repositories of software that users can currently choose to run on Android devices, of which the best known is F-Droid.
There’s no evidence that apps distributed through F-Droid are more likely to contain poorly-disclosed surveillance or other malware than the apps distributed through the Google Play Store (or the Apple App Store). The reverse is more likely. Because the F-Droid repository includes only open-source apps, the F-Droid team can and does — unlike Google — check that “anti-features” are prominently disclosed:
When a developer creates an app and hosts the source code publicly somewhere, the F-Droid team reviews it, inspecting it to ensure that it is completely open source and contains no undocumented anti-features such as advertisements or trackers. Once it passes inspection, the F-Droid build service compiles and packages the app to make it ready for distribution. The package is then signed either with F-Droid’s cryptographic key, or, if the build is reproducible, enables distribution using the original developer’s private key.
F-Droid’s warnings that an app a user is about to download contains anti-features such as trackers, and what those anti-features are, are far more conspicuous than any of the information available through the Google Play Store about similar app anti-features.
If Google makes good on its threats to demand scanned images of app developers’ government-issued IDs, it’s unclear whether users will still be able to install apps from F-Droid on “Google-certified” devices at all, even if they use alternate builds of the open-source components of Android, such as GrapheneOS or LineageOS.
A software arms race is likely between Google and independent app and operating system developers. Ways will probably be found to work around Google’s attempts to exert more control over what software we can run on our devices. But by demanding ID from developers, and trying to shut down independent software repositories, Google is hurting, not helping, users who are seeking apps and devices with fewer hidden trackers.