How the NSA obtains and uses airline reservations
A front-page report in today’s New York Times based on documents leaked by NSA whistleblower Edward Snowden confirms that the NSA, like the DHS, uses airline reservation data as part of its profiling and social network analysis of US citizens and foreigners. Today’s report also raises new questions, and suggests some answers, as to how the NSA obtains and uses this airline data.
The Times’ report today on NSA social network analysis mentions that:
The [NSA] can augment the communications data with material from public, commercial and other sources, including … passenger manifests…, according to the documents. They do not indicate any restrictions on the use of such “enrichment” data, and several former senior Obama administration officials said the agency drew on it for both Americans and foreigners….
[T]he N.S.A. correlates 164 “relationship types” to build social networks and what the agency calls “community of interest” profiles, using queries like “travelsWith“.
In their most basic form, passenger manifests list each passenger individually and do not indicate which passengers were traveling together. At a minimum, either “Advance Passenger Information” (API) data, some other source of “enhanced” passenger manifest data, or complete Passenger Name Records (PNRs) would be needed to identify which passengers on a given flight had reservations in the same PNR (a single PNR can contain the reservations for an entire party or group traveling together) and thus who “travelsWith” whom.
We’ve long known that the DHS collects API and PNR data about US citizens and foreigners alike, compiles this data in its Automated Targeting System and Secure Flight databases, and mines this data both to target individuals (including journalists and activists) and for social network analysis (correlating e.g. telephone numbers and airline reservations) to identify and target new suspects on the basis of their association with current suspects (i.e. as a suspicion-generating or guilt-by-association system).
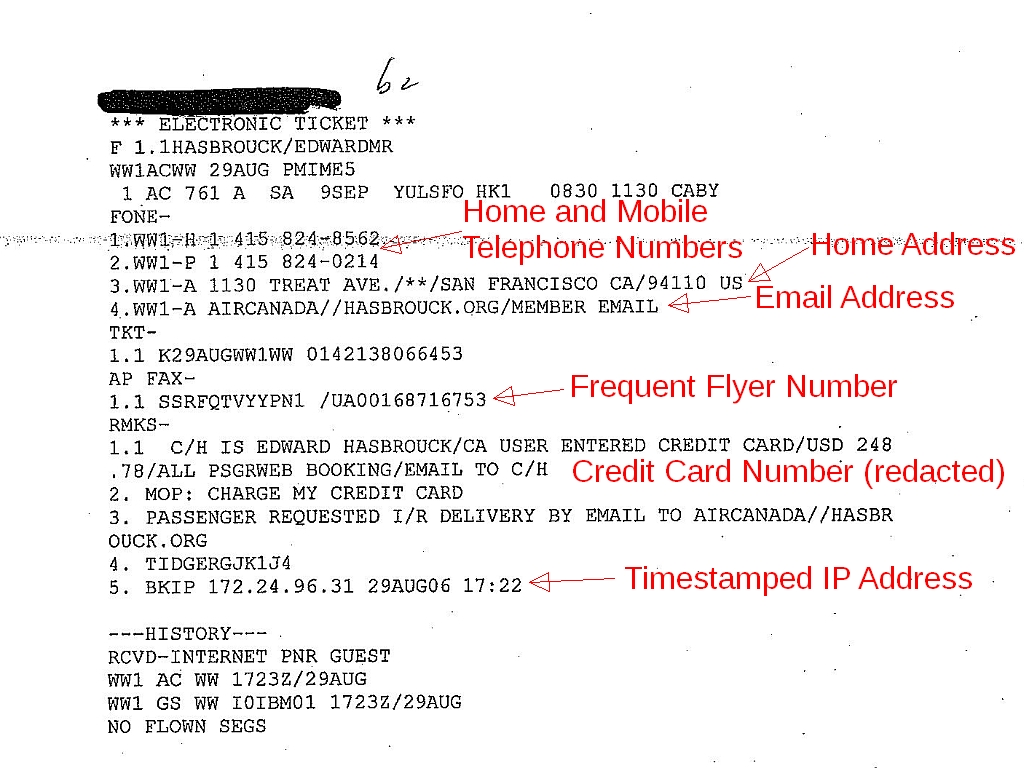
A typical PNR like the one shown above (from a DHS Automated Targeting System dossier; click the thumbnail for a larger image) includes a timestamped IP address (line 5 of the “remarks” in the example above), email address, home address, credit card number, mobile phone number, etc., so it can readily be correlated with Internet, communications, and financial records.
The NSA would presumably have been interested in flights worldwide, including flights within parts of the world far from the USA, while the DHS claims to collect PNR data only for flights to, from, within, or via the US. But we know that the DHS can, and sometimes does, collect PNR data about flights elsewhere.
As we reported in 2007, and as was mentioned in a front-page story in the Washington Post based on our research, ATS records released by DHS in response to our requests (you can request your own ATS file using the forms here) confirmed that the DHS already had “root” access to the computerized reservation systems (CRSs), so that the DHS could retrieve any PNR in those CRSs, even if it didn’t include any US flights.
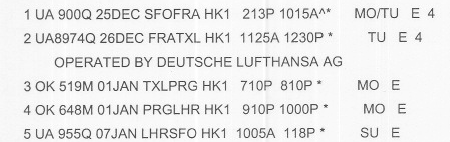
The “smoking gun” confirming DHS root access to CRSs was this PNR for someone who traveled from San Francisco to Berlin (TXL) on United Airlines and a United/Lufthansa codeshare flight, stayed in Berlin for six days, continued from Berlin to London (LHR), stayed in London for another six days, and then returned to SFO on United:
The portion of the journey from Berlin to London via Prague was on Czech Airlines (OK), an airline which does not (and did not then) fly to, from, or via any point in the US. Additional details in the PNR showed that a separate ticket was issued for the OK flights, which did not connect to flights to or from the US. A CRS user with a United Airlines user ID and privileges would not have been able to see these flights. Only a user with an ID from the travel agency that made these reservations, or a user with “root” privileges (such as a user with an ID from the CRS company), would have been able to see all of the data that the DHS was able to see and import into ATS.
So could the NSA have obtained its copies of PNR and/or API data from DHS, or by using the root-user credentials that CRS companies had provided to the DHS? Maybe. Since neither DHS nor the CRSs keep logs of who accesses their respective copies of PNR data, there’s no way to know for sure except through leaks or the testimony of whistleblowers.
But we suspect that the NSA has some way to obtain PNR and/or API data independent of the DHS.